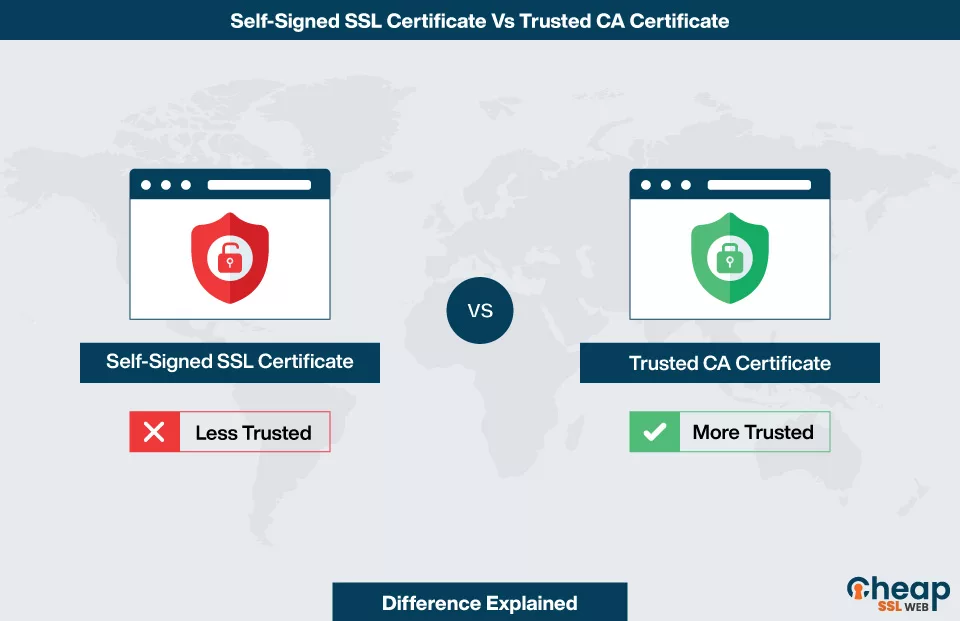
Self-signed certificates are suitable for internal (intranet) sites, and sites used in testing environments. CA certificates, on the other hand, are suitable for all public-facing websites and software.By default, self-signed certificates will never be trusted by web browsers and operating systems. It is up to each user to bypass the security warning by manually approving each self-sign certificate they encounter, on each device they use, on a case-by-case basis.The key difference is: the self-signed certificate is signed by the same party that owns the private key, while the digital identity certificate returned by the certificate authority upon receiving the certificate signing request is signed using the certificate authority's private key.
What is the purpose of self-signed certificate : Depending on what the certificate is being used for, a self-signed certificate is a certificate signed by the same user or device using that certificate. This works for code being signed for internal use, or for an application being used by the creator, but not for software that is being used by external users.
Why can’t a self-signed certificate be trusted
Not trusted by browsers and users
Self-signed certificates contain private and public keys within the same entity, and they cannot be revoked, thus making it difficult to detect security compromises.
What are the disadvantages of a self-signed certificate : Limitations and considerations
- Lack of trust validation: The major drawback of self-signed certificates is the absence of trust validation.
- Risk of compromise.
- Manual trust establishment: Users must manually verify and trust self-signed certificates by adding them to their trust stores.
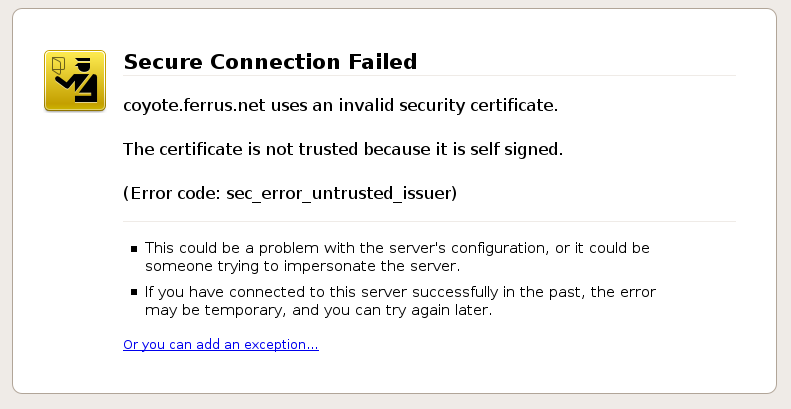
Self-signed certificates aren't trusted by browsers because they are generated by your server, not by a CA. You can tell if a certificate is self-signed if a CA is not listed in the issuer field in our SSL Certificate tester.
One possible cause of this error is that a self-signed certificate is installed on the server. Self-signed certificates aren't trusted by browsers because they are generated by your server, not by a CA. You can tell if a certificate is self-signed if a CA is not listed in the issuer field in our SSL Certificate tester.
What is the biggest issue with a self-signed certificate
Disadvantages of using Self-signed SSL Certificates
Since a publicly trustworthy CA does not sign self-signed certificates, browsers and operating systems do not trust them. Browsers wouldn't display the green lock icon or other trust-related visual cues. There will always be a “Accept Risk” prompt in opening websites.On Chrome. Let's click on the “Import” button and locate and select our self-signed certificate. Once the import is done, we need to restart Chrome and our self-signed certificate will be trusted on Chrome.Since self-signed certificates aren't issued by a trusted CA, they will trigger security warnings in web browsers, potentially causing trust issues for users. Setting up and managing self-signed certificates can be more complex, especially for non-technical users.
Self-signed certificates aren't trusted by browsers because they are generated by your server, not by a CA. You can tell if a certificate is self-signed if a CA is not listed in the issuer field in our SSL Certificate tester.